Table of contents [Show]
Have you ever heard of an application called TOR Browser? We tend to be more familiar with browsers like Google Chrome, Mozilla Firefox, Opera Mini, Microsoft Edge, and the like.
However, TOR Browser has capabilities that other browsers do not. We've summarized everything in the explanation below.
So, if you're curious about how to use TOR Browser, check out the review here.
What is TOR Browser?

Many people may not yet know what TOR (The Onion Router) Browser is. In general, this application is almost the same as other common browsers like Google Chrome, Firefox, or Opera.
However, TOR has some unique features, particularly concerning privacy and security that other browsers do not offer. TOR optimizes the privacy and security of its users.
How secure is their user protection system? TOR employs a multi-layered approach to hide users' traffic and true identities.
Similar to the name's philosophy, it's compared to an onion, which has multiple layers. This symbolizes the multiple layers of security protecting users from suspicious activities.
How TOR Browser's Security Works
TOR Browser uses an anonymous system that operates on a special network consisting of many servers.
When you use the browser, the system randomly selects three relays connected to the internet.
Each relay goes through an encryption process, resulting in the relay only reading the IP at the endpoints.
With this layered security method, the internet traffic you use is not easily traceable by others through your IP.
Unfortunately, this capability impacts internet access speed for certain website content. When you open a site, for example, an international website, the relay spreads across several countries before reaching the main site.
You can observe this layered security system when opening a site. Click on the padlock icon next to the URL address. There, you'll see several IP addresses from different countries.
Periodically, the IP addresses change randomly and repeatedly while you keep the site open.
Advantages of TOR Browser
Compared to other browsers, TOR has unique features in terms of privacy and security. This is the main reason why you should use TOR Browser.
Here are the advantages summarized in several points:
- Access foreign content freely.
- Open blocked sites or websites without censorship.
- Multi-layered security so the device's IP cannot be known by others.
- Much safer than standard privacy browsers.
- Available on multiple platforms, including Windows, iOS, Linux, and Android.
Disadvantages of TOR Browser
Aside from its advantages, TOR also has some disadvantages, which you can compare to determine if it’s worth using.
- Internet speed tends to be slower because it has to go through several layers of IP placed in random countries.
- Less efficient for spoofing the device's IP address because VPNs are much more practical.
- No developer support or responsible party.
How to Install TOR Browser
Getting the TOR Browser application is very easy. You can find the installation file on their official website for free.
The installation process is also simple, similar to installing other browser applications. Here's how:
- Visit https://torproject.org/download
- Choose the appropriate file for your OS, such as Download for Windows.
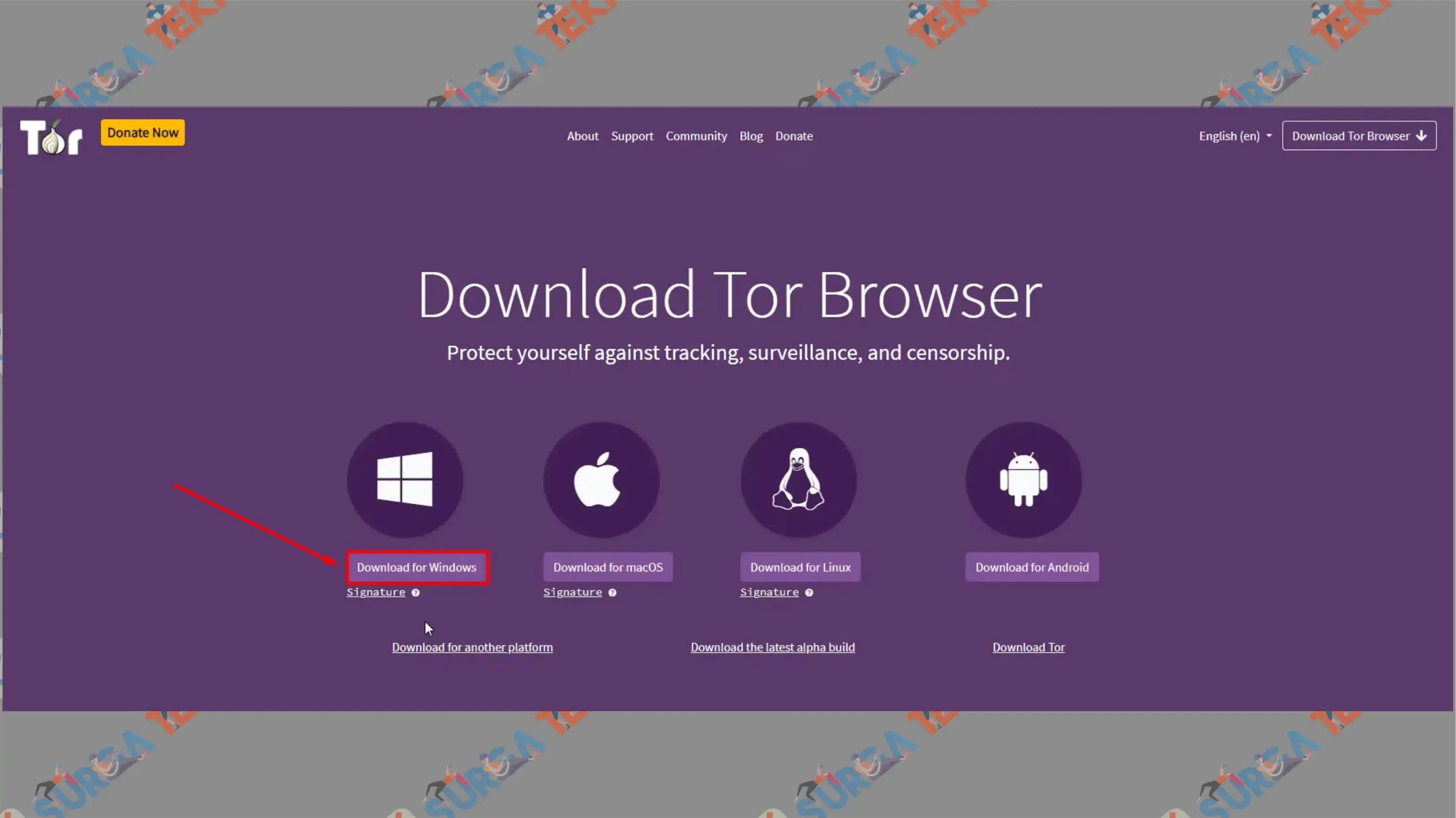
- Wait for the process to complete.
- Go to the download folder and find the installation file.
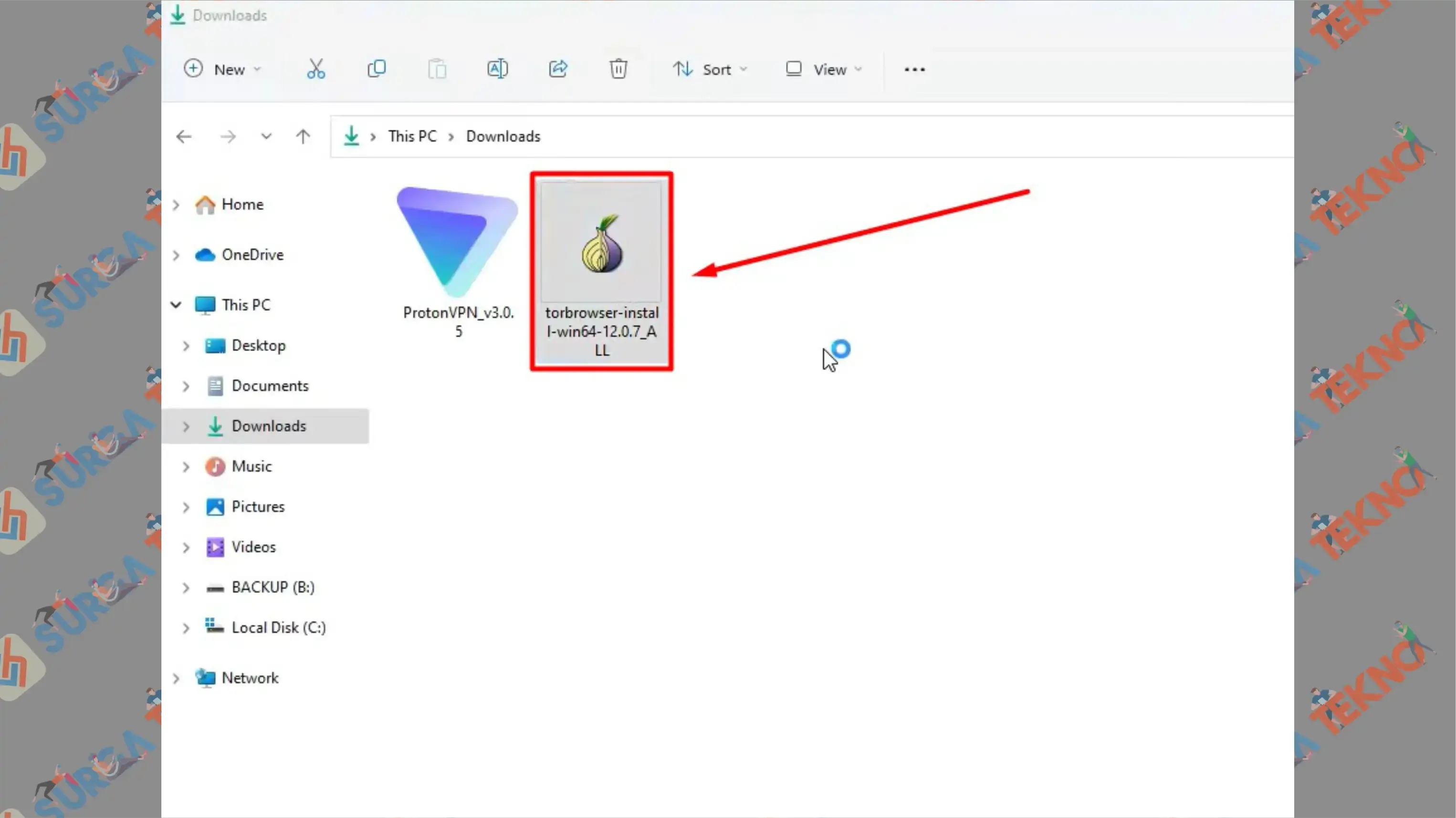
- Double-click the TOR Browser executable file.
- First, choose the language, then continue to select the installation location, and click Install.
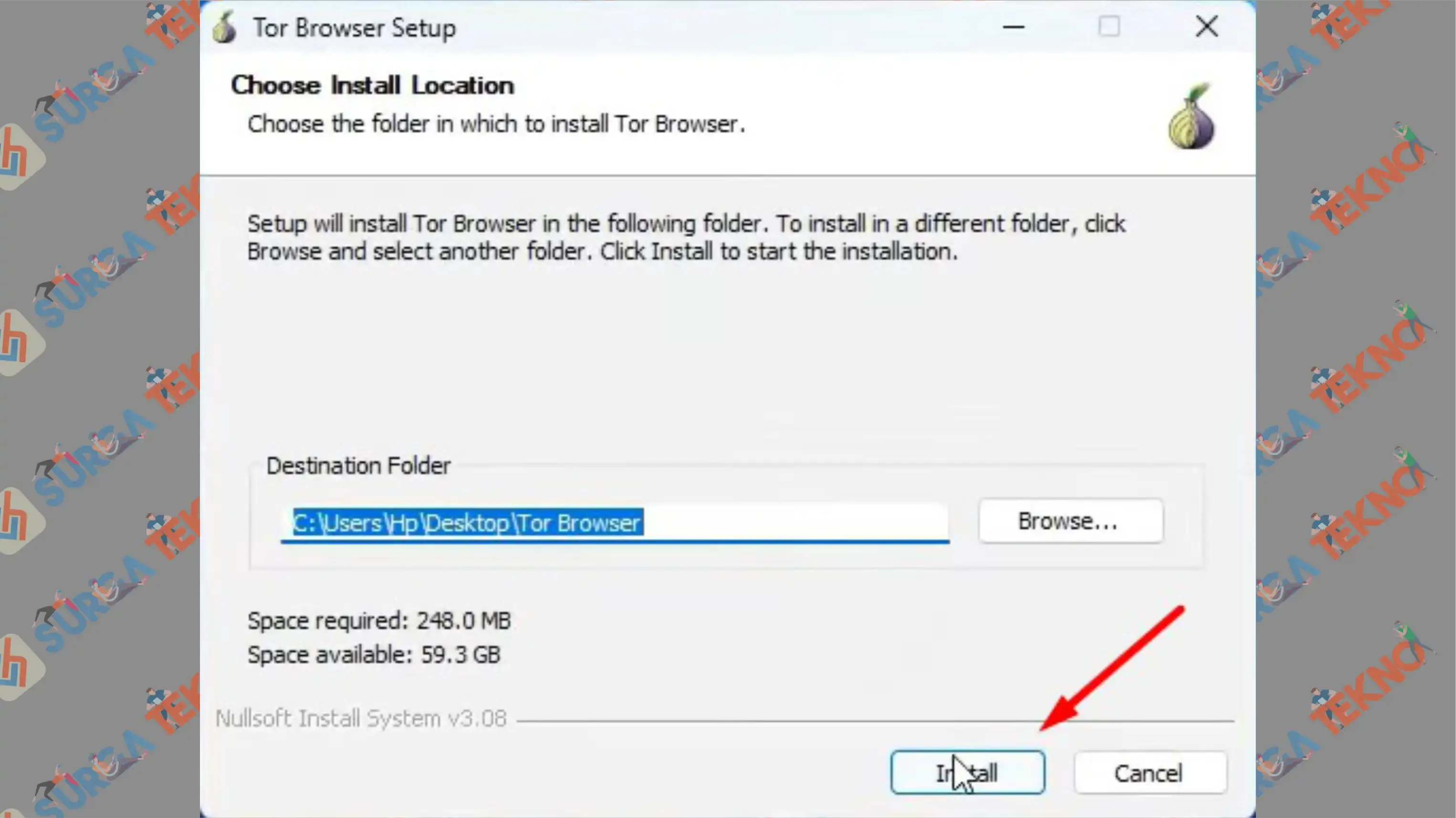
- Finally, once installed, just run the application.
- Done.
Conclusion
That's a brief explanation of TOR Browser, including its definition, how to use it, its advantages, disadvantages, and the installation process.
With this browser, you can freely access any site without censorship limits because it is equipped with a multi-layered IP protection system. Hope this helps.




